The Net Protector Endpoint Security (NPAV EPS) Dashboard serves as the central management console for an organization’s endpoint protection infrastructure. Designed for both on-premise and cloud deployments, it provides administrators with a comprehensive, real-time overview and granular control over network security, facilitating efficient monitoring, management, investigation, and response to cyber threats across all connected endpoints.
Key Features and Functionalities
The NPAV EPS Dashboard presents a web-based, graphical interface that distills complex security data into actionable insights, enabling proactive threat management and policy enforcement.
1. Centralized Management and Monitoring:
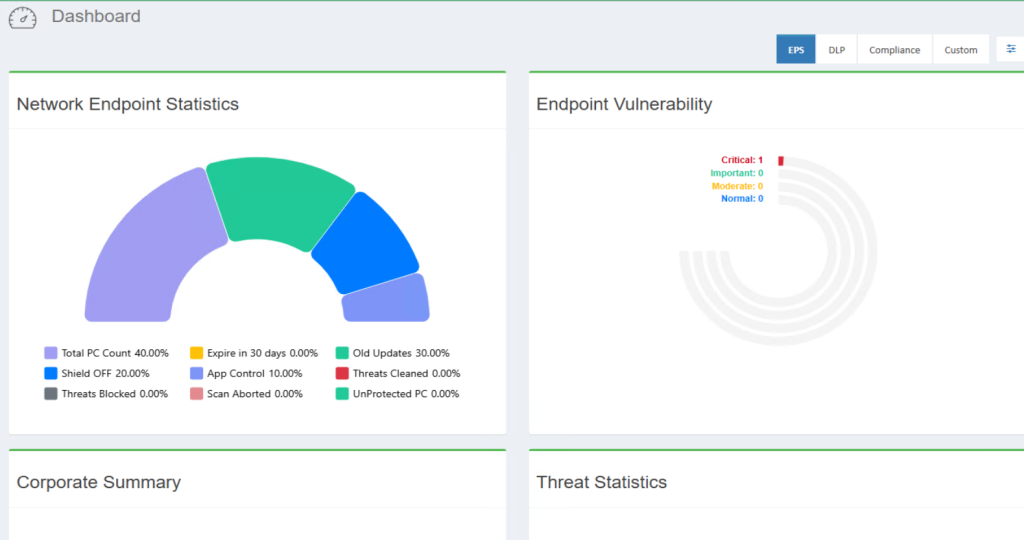
- Network Endpoints Statistics: Provides a high-level overview of all connected endpoints, including their online/offline status, security health, and vulnerability posture.
- Graphical Dashboards: Utilizes intuitive charts and graphs for real-time visualization of network endpoint statistics, security health status, client updates, and threat status. This includes a clear representation of protected and unprotected client PCs.
- Multi-Location and Multi-Device Management: Allows administrators to manage security for PCs across various branches and locations from a single console, providing a unified view of the entire network.
- Real-time Alerts and Notifications: Generates immediate alerts for critical security events, such as low disk space (with options for WhatsApp and email alerts), enabling prompt intervention.
2. Threat Detection and Response:
- Threat Status and Statistics: Displays real-time information on detected threats, including types of malware, ransomware attacks prevented, and malicious URLs blocked.
- Vulnerability Scanning: Scans and lists exposed areas on all network endpoints and roaming devices, aiding in proactive vulnerability management.
- Behavior Heuristic Detection: Detects and blocks ransomware heuristically, protecting systems from network and endpoint-originated infections.
- Anti-Ransomware Shield: Provides specialized protection against ransomware attacks, safeguarding data from encryption and corruption.
- Anti-Phishing: Blocks fraudulent and phishing websites, preventing credential theft and data breaches.
- IDS/IPS Protection: Detects malicious network activities exploiting application vulnerabilities and blocks intruder attempts on managed endpoints.
3. Policy Management and Control:
- Device Control: Offers comprehensive access control and monitoring for various device types, including USBs, Bluetooth, and portable devices. It supports offline enforcement and forensics, allowing for granular control (Allow/Block/Read-Only) based on vendor ID, product ID, and serial number.
- Application Control: Enables administrators to view, manage, and enforce policies for running processes and applications on client machines. This includes the ability to kill, block, or unblock processes, and to approve or block specific applications to enhance productivity.
- Web Protection: Blocks unwanted sites, videos, MP3s, and torrents, improving endpoint productivity and enforcing Browse policies.
- Firewall Management: Monitors and blocks malicious incoming and outgoing internet connections, allowing administrators to easily add and manage rules based on ports, IP addresses, and applications.
- Policy Creation and Assignment: Facilitates the creation and application of security policies for individual PCs or groups, with options for “Audit Mode” to verify policies before full enforcement.
- Password Management: Secures and automates the process of managing local administrative passwords on endpoints, allowing administrators to set endpoint passwords remotely.
4. Data Protection and Management:
- Data Backup: Manages client data backup from the server, protecting against ransomware attacks and ensuring data integrity.
- File Sharing Activity Monitoring: Efficiently monitors and logs activity on managed endpoints related to file sharing, including details such as user names, file names, and client IP addresses.
- Printer Activity Monitor: Tracks and logs printing tasks, providing details like document name, number of copies, date, time, IP, and machine name.
- Data Loss Prevention (DLP): Offers advanced DLP capabilities to prevent unauthorized leaks of sensitive information, with detailed reports on data origin and destination. It works across various browsers, email clients, and protocols (HTTP, FTP, POP3, SMTP).
- Disk Encryption: Provides file-level, folder-level, volume-level, and full disk encryption to secure data, even if the disk is lost or stolen.
- Remote Data Wiper: Allows for the secure deletion of data in selected folders, preventing recovery using forensic tools.
5. System Health and Optimization:
- Automatic Updates: Ensures continuous protection with hourly, automatic updates of antivirus definitions. The system also supports offline updates for environments without direct internet access.
- System Tuner: Optimizes system performance by identifying and removing unnecessary resources, repairing the Windows Registry, and freeing up disk space. Scheduled tune-ups and monthly disk checks are available.
- Asset Management: Provides an easy way to list and track system hardware components across the network.
- Session Activity Monitoring: Records details of login/logout, remote desktop, and system startup/shutdown activities, aiding in monitoring endpoint usage.
6. Reporting and Auditing:
- Comprehensive Reports: Generates detailed and summary security reports for the network, including application usage reports (with details like file name, path, publisher, and launch count).
- Audit Logs: Provides detailed logs related to events, file transfers, device usage, and unusual user activity, essential for incident prevention and mitigation.
- SIEM Integration: Supports integration with Security Information and Event Management (SIEM) systems for custom reports, dashboards, and user behavior analysis.
User Interface Description
The Net Protector Endpoint Security Dashboard is designed for clarity and ease of use, featuring a web-based console with a focus on graphical representation. The interface typically includes:
- Navigation Pane/Menu: Located on the side or top, providing quick access to different modules such as Dashboard, Endpoints, Policies, Reports, Settings, etc.
- Main Dashboard View: The central area displaying key security metrics through interactive charts and widgets. This includes visual summaries of network health, threat landscapes, and update statuses.
- Tabbed Interface: Many sections, like Application Control, utilize tabs for different functionalities (e.g., “App Control,” “Blocked List,” “Approved Apps,” “Reports Tab”).
- Filter and Search Options: Allows administrators to quickly locate specific endpoints, policies, or events.
- Action Buttons and Wizards: Intuitive controls for initiating scans, applying updates, creating policies, and performing remote actions on endpoints.
- Detailed Views: Clicking on summary information often drills down to more granular details, such as a list of infected machines or specific policy configurations.
In conclusion, the Net Protector Endpoint Security Dashboard is a robust and intuitive management platform that provides organizations with the tools necessary to maintain a strong security posture, protect sensitive data, and ensure business continuity in an ever-evolving threat landscape. Its centralized control, comprehensive reporting, and extensive policy enforcement capabilities make it a vital component for effective endpoint security management.

