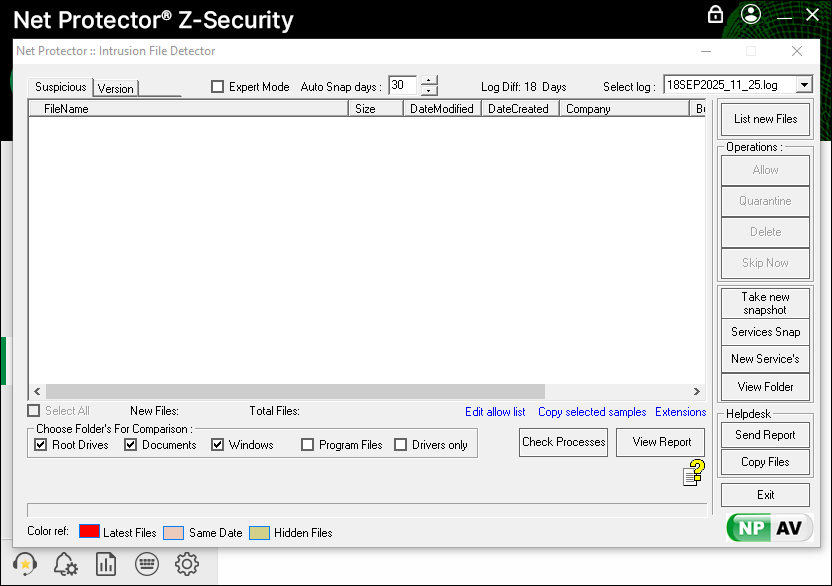
The IDS you described is designed to detect unauthorized or suspicious changes in key system files. By monitoring modifications or newly created files, it can alert administrators to potential malware infections, ransomware, or other intrusions.
How It Works
- Snapshot Creation:
- The system first takes a snapshot of important directories, in this case:
- C:\Windows\System32C:\Program Files
- The snapshot includes metadata like file names, sizes, timestamps, and sometimes hashes (MD5, SHA-1, etc.).
- The system first takes a snapshot of important directories, in this case:
- Monitoring Period:
- The IDS checks for files modified or created in the last 10 days.
- This time-based filter reduces noise from legitimate system updates while focusing on recent changes.
Benefits
- Detects new malware that modifies or drops files in system-critical directories.
- Tracks unauthorized changes by suspicious programs or attackers.
- Helps with compliance audits, since some regulations require integrity monitoring.